Optimize the “hunting-group” service
The “hunting group” is a long-established enterprise communication service that was widely used in the circuit-switched telephone era and remains deployed by many businesses even in the VoIP era. However, times have changed, and the service itself must evolve to keep pace with the characteristics and requirements of IP networks. Based on recent customer needs and changes in the network environment, we have implemented several optimizations to the hunting group feature in miniSIPServer.
The focus has been on modifying and optimizing the “Operator” feature within the service. Please refer to the image below:
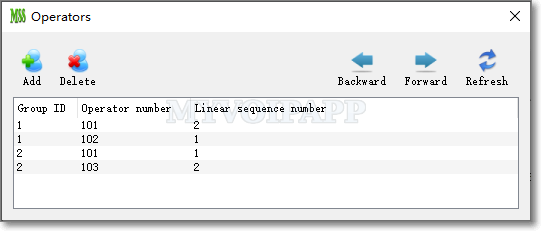
Change 1: One operator can now be assigned to multiple hunting groups simultaneously. Previously, an operator was restricted to a single hunting group, which no longer meets the needs of modern enterprises. As employees often handle multifaceted roles, there is a significant need for them to support multiple hunting groups at the same time. This new feature addresses this requirement.
During the era of circuit-switched telephony, phone terminals lacked sufficient capabilities. Therefore, hunting groups typically allowed operators to log in or out by dialing specific codes. However, for the following reasons, the new hunting group feature in miniSIPServer no longer supports manual operator login or logout:
(1) Most modern SIP terminals now have sufficient functionality to implement features like “Do Not Disturb” directly on the device side, making manual login/logout unnecessary.
(2) Now that one operator can support multiple hunting groups simultaneously, simple login/logout actions are inadequate. Operations would need to be performed for specific hunting groups, making dialing procedures cumbersome and unnecessary.
Change 2: For hunting groups using the “Linear” policy, operators can now be assigned a sequence number to define their selection order. Previously, the selection order was based solely on the sequence in which operators logged into the system, which essentially resulted in a random order and could not meet practical requirements. In real-world scenarios, certain operators often need different priority levels within the group.
An operator with a smaller “Linear sequence number” will be selected earlier by the hunting group. If multiple operators have the same sequence number, they will be sorted by their login time, with those who logged in earlier receiving priority.
Of course, this new configuration does not apply to the “round-robin” strategy. The round-robin strategy always strives to distribute calls as evenly as possible among operators to balance the workload.
The hunting group feature has been updated in both the on-premises and cloud versions of miniSIPServer. There are no differences in configuration or usage between the two versions. Please refer to the product documentation for more detailed information.